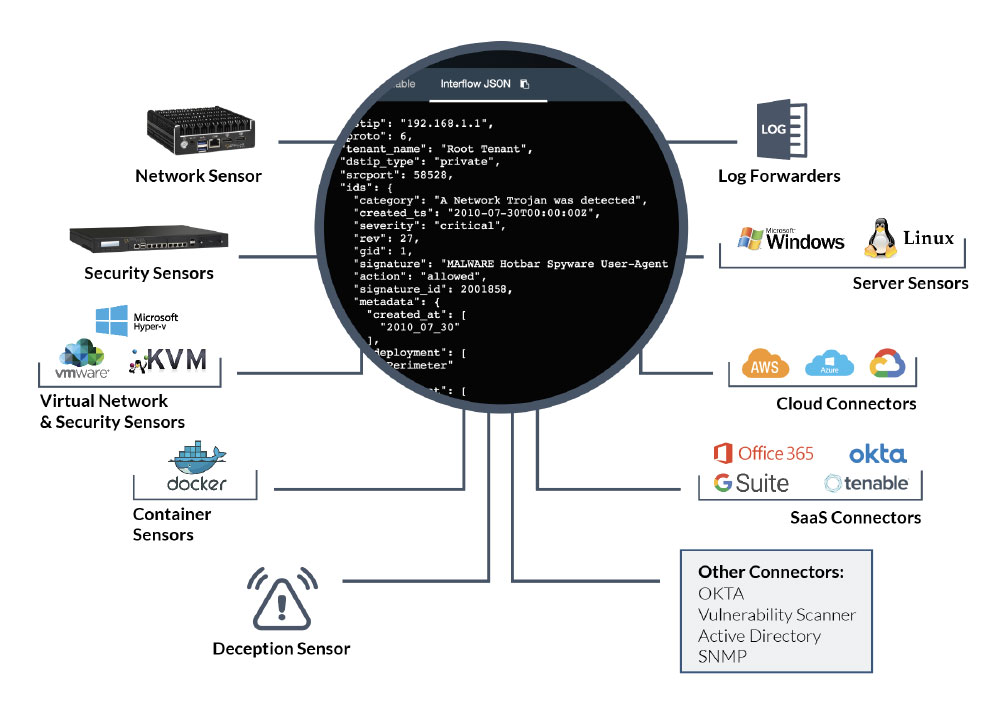
Types of Stellar Cyber Sensors
This topic describes the family of sensors available from Stellar Cyber, from lightweight server sensors that install as agents on target Linux and Windows servers to purpose-built physical sensors capable of monitoring at 10G network speeds. Sensors provide the data gathering foundation for Stellar Cyber's OpenXDR platform, gathering the right data with context.
Sensors are used to create visibility where it does not yet exist, or to simplify and consolidate telemetry collection with Stellar Cyber. You can capture data from network, assets, and containers, all under the same license, and administered from the same platform.
Starting with the 4.3.7 release, new physical sensors are shipped as modular sensors on Ubuntu 22.04.
Family of Stellar Cyber Sensors
The Stellar Cyberfamily of sensors consists of the following members:
-
Server Sensors – Server Sensors install as software on target hosts to be monitored. They are also referred to as agents. Server Sensors are available for both Linux and Windows, as described below.
-
Device Sensors – Device Sensor is an umbrella term that refers to any purpose-built Stellar Cyber sensor that includes both the host and the Stellar Cyber monitoring software. Device Sensors are provided as both physical devices (Photon sensors) and virtual machine images for different target environments.
Previous releases provided a variety of different types of device sensors, including Network, Security, and Modular. Starting with 4.3.7, the only type of device sensor is Modular. You can use the Modular Sensor Profile to enable whatever sensor features you like, creating the same functionality provided by the different sensor types in previous releases. For your convenience, both Modular sensors and the legacy Network and Security sensors are described below.
Linux Server Sensor
A Linux server sensor is a managed background daemon that works as a modular sensor without log forwarding that also monitors:
- Process info
- Command execution
- Files
- File events
The server sensor converts that information to metadata and forwards it to the DP as Interflow. The DP can then correlate traffic, processes, users, and commands for security, DDoS, and breach attempt detections.
The server sensor launches the following processes:
aella_audit—collects audit logs and provides file integrity monitoringaella_conf—handles the configurationaella_ctrl—monitors other services, and can stop or start them based on the configurationaella_flow—collects metadata in trafficaella_mon—collects system resource usage, including CPU, RAM, and disk
Data collected by the Linux Server Sensor can feed the following Stellar Cyber indices:
-
Traffic (
aella-adr-*) -
Linux Events (
aella-audit-*) -
Sensor Monitoring (
aella-ade-*)
Windows Server Sensor
The Windows Server Sensor (agent) runs as a Windows service in a compatible Windows Server system. The Server Sensor observes events within the Windows Server system and sends Interflow data records to the data processor.
The captured events are:
- Hardware
- Security
- System
- Windows Firewall
- Windows Defender
- PowerShell
The Windows Server Sensor launches the following processes:
|
Name in Task Manager |
Name in Services App |
Description |
|---|---|---|
|
aella_conf_win_srv.exe |
Windows Agent Sensor Conf |
Handles Windows Server Sensor configuration |
|
aella_ctrl_win_srv.exe |
Windows Agent Sensor Ctrl |
Monitors other services, and can stop or start them based on the configuration |
|
aella_winlog.exe |
Windows Agent Sensor Logbeat |
Sends Windows events to DP |
|
aella_filebeat.exe |
Windows Agent Sensor Filebeat |
Sends log files from Windows DHCP server (if installed and running) to DP |
|
aella_fim.exe |
Windows Agent Sensor FIM |
Provides file integrity monitoring services, as configured in the Sensor Profile |
|
aella_diagnostics_win_srv.exe |
Windows Agent Sensor Phonehome |
Sends Windows Server Sensor logs to DP |
Modular Sensor
A modular sensor lets you easily add the features you like to your sensor. This helps simplify your deployment and lets you manage the VM requirements for the sensors based on the modular features they use.
Modular Sensors always include log ingestion. From there, you can enable different features as part of your modular sensor profile:
-
Enable the Network Traffic feature to monitor the virtual environment, the physical environment if connected to the span port of a physical switch, or the LAN segment via a mirror port on a switch. The sensor monitors network and server response times and can identify applications.
The sensor converts that information to metadata and forwards it to the DP as Interflow. The DP can then provide security, DDoS, and breach attempt detections.
-
Enable the Sandbox and IDS features to improve your security posture:
- Sandbox lets you detect malware in files and network traffic through Stellar Cyber's integrated cloud service and also provides anti-virus services.
- IDS lets you detect intrusion attempts using both files and network traffic.
Keep in mind that VM resource requirements increase as you add more features to the Modular Sensor Profile. Refer to Modular Sensor Specifications for details on the resources required to run different combinations of features in a Modular Sensor Profile, as well as how to use the show module and show module request CLI commands to compare provisioned resources against those required to run specific feature combinations. Stellar Cyber only enables a Modular Sensor Profile on a sensor if the host VM's resources can support it.
Network Sensor
Previous releases provided purpose-built Network Sensors that have now been replaced by Modular Sensors. \You can use the Modular Sensor Profile to enable the features that corresponded to a Network Sensor in previous releases.
In previous releases, network sensors monitor the virtual environment, the physical environment if connected to the span port of a physical switch, or the LAN segment via a mirror port on a switch. The sensor monitors network and server response times and can identify applications.
The sensor converts that information to metadata and forwards it to the DP as Interflow. The DP can then provide security, DDoS, and breach attempt detections.
You can configure a Modular Sensor to provide the functionality associated with Network Sensors in previous releases by enabling the Network Traffic option in its Modular Sensor Profile.
Network sensors collect metadata from physical or virtual switches and can aggregate logs. They are available as either physical devices or virtual images for common cloud environments.
Security Sensor
Previous releases provided purpose-built Security Sensors that have now been replaced by Modular Sensors. You can use the Modular Sensor Profile to enable the features that corresponded to a Security Sensor in previous releases.
A security sensor operates as a sensor with the Network Traffic feature enabled and adds:
- sandbox
- anti-virus
- IDS
You can also tunnel traffic over VXLAN from a server sensor or Modular Server with the Network Traffic feature enabled to a sensor with the Sandbox and IDS options enabled so it can inspect those environments.
You can configure a Modular Sensor to provide the functionality associated with Security Sensors in previous releases by enabling the Sandbox and IDS options in its Modular Sensor Profile.